Introduction
Since the outbreak of the Covid-19 pandemic, employees have become all too familiar with the Work From Anywhere (WFA) and Work From Home (WFH) experience. According to a recent PEW Research Center survey, 20% of the workforce was already working from home prior to the Covid-19 outbreak. Of the people whose job could be fully or mostly performed remotely, 73% of them preferred to WFH, and those who preferred to continue WFH after the coronavirus was over were 54%. Lastly, 87% of people agreed that the right equipment and technology made their transition somewhat or very easy.
WFH is not new. Many organizations, such as educational institutions, have already been using this employment model. However, the coronavirus forced executives to adopt WFA for all or some of their employees. Some organizations are still planning to make their remote work permanent. Harvard Business Review revealed that some companies are seriously evaluating this as a viable option. These companies include the State Bank of India, Siemens, Shopify, Facebook, and Twitter.
In this blog post, we will delve into the detail of how on-site employees are being shifted to remote positions, the serious cyber threats to distributed data, and protecting data in a WFA environment.
Shifting On-Site Employees to Permanent Remote Positions
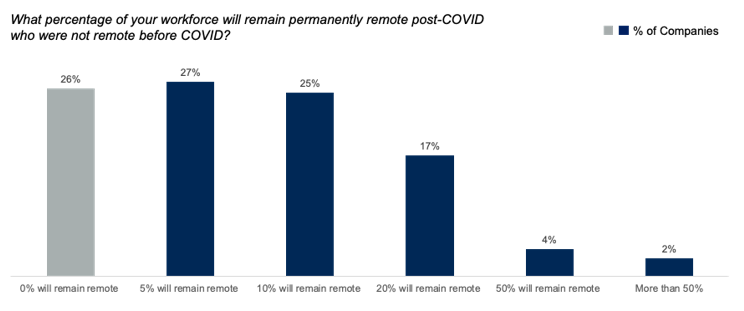
According to Spotify’s WFA initiative, employees have the option to work either from their home or the office. Even they can choose a geographic location of their own liking. As per the Gartner report, most finance leaders planned to shift some of their previously on-site employees to permanent remote positions after the pandemic. The following is a graphical representation of this report.

Cyber Threats to Distributed Data
Since business data is now anywhere and everywhere, the WFA model demands an effective cybersecurity strategy. Confidential information, personally identifiable information, and other sensative data is now in motion outside the company’s control and can be intercepted by cybercriminals to compromise its confidentiality. As a result, hackers attempt to exploit sensitive information, including cloud documents, attachments, emails, instant message clients, and third-party services. Phishing scams and Man-in-the-middle (MITM) attacks, and other cyber-attacks are prevalent and very dangerous. Social engineering attacks, including phishing, have become the norm.
Remedies: How to Protect Your Company?
The cybersecurity environment is changing and adapting to the shift from WFH to WFA, and the broader distribution of the workforce expands the attack surface making sensitive data even more at risk. Therefore, organizations must take proactive measures to save their employees against data breaches.
- Create a Bring-Your-Own-Device (BYOD) policy designed to thwart attacks. BYOD can be an employee’s personal laptop, mobile device, iPad, or tablet. According to CISO’s Benchmark Report 2020, businesses are endeavoring to manage the smartphones and other mobile devices of their remote workers.
- Use Two-Factor Authentication (TFA) for personal devices.
- Use virtual Security Operation Centers (SOC) to protect remote workers
- Install antivirus and internet security suites at home
- Deploy a Virtual Private Network (VPN) for a network connection
- Disable the webcam when not in use to prevent video recording or image leakage during the attack.
- Increase the security of your home WiFi.
- Use a centralized storage solution with encryption.
- Require cybersecurity awareness training for you and all your employees that includes training against social engineering attacks especially phishing scams.
- Use a password manager that enforces strong passwords for your login accounts. The password should be at least 14 characters. Use letters, numbers, uppercase and lowercase letters, functional keys, and their combination.
References
- https://hbr.org/2020/11/our-work-from-anywhere-future
- https://www.gartner.com/en/newsroom/press-releases/2020-04-03-gartner-cfo-surey-reveals-74-percent-of-organizations-to-shift-some-employees-to-remote-work-permanently2
- https://www.kaspersky.com/resource-center/threats/remote-working-how-to-stay-safe
- https://www.itgovernance.co.uk/blog/the-cyber-security-risks-of-working-from-home



